In my recent webinar on “MBSE and the Cloud: A Model of IT Delivery” one of the attendees asked how the type of model I had developed in could be used to support cybersecurity. In this post I will discuss how the MBSE model of the Learning Management System could be used to capture information relevant to implementing cybersecurity for the final design. Although this example uses CORE a similar approach could be used with GENESYS.
A firewall is typically the first line of defense for our computers and networks to help prevent undesired access from outside. A firewall mitigates threats by monitoring traffic entering or leaving a computer or network and disallowing unauthorized traffic. Typically firewall rules need to be specified in terms of IP addresses, port number, and whether traffic is allowed/disallowed for the various sources and destinations. In this example I will show how we can capture some of this relevant information in our model using CORE. [Note, in this example I will focus on the typical service listening ports rather than the ephemeral ports that maybe used for responses once a service has been requested.]
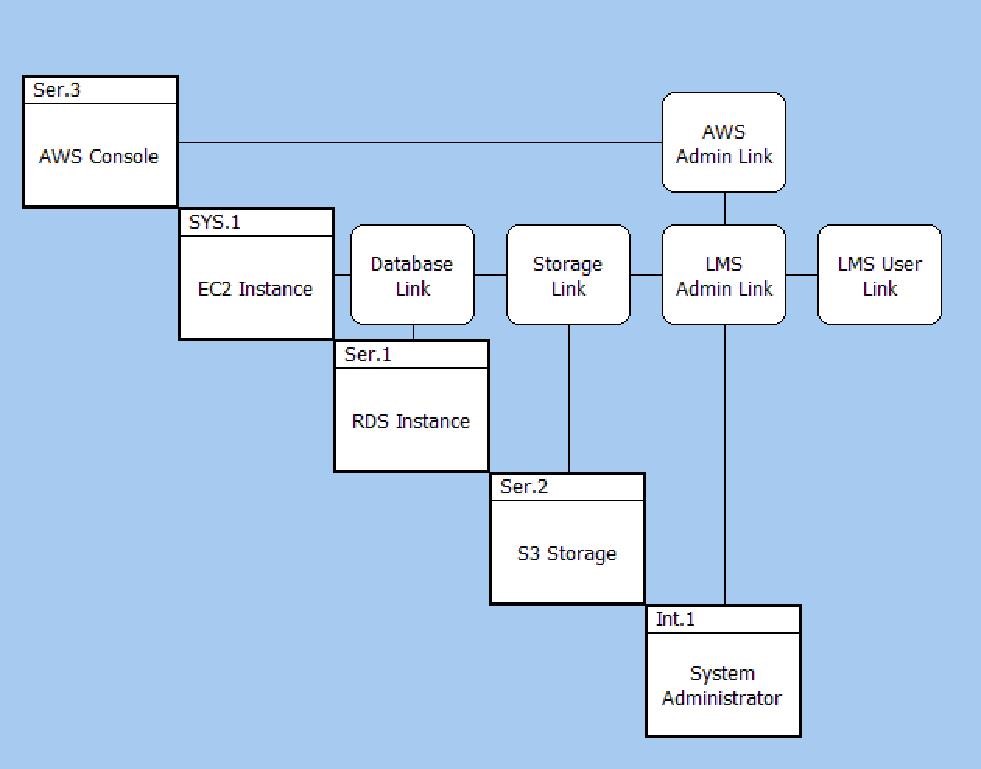
The Component hierarchy below shows the structure of the solution and its relationship to the context and an external actor, in this case a User. I have included the System Administrator within the solution as the practices and procedures for the system administrator are going to be an output from the solution design.
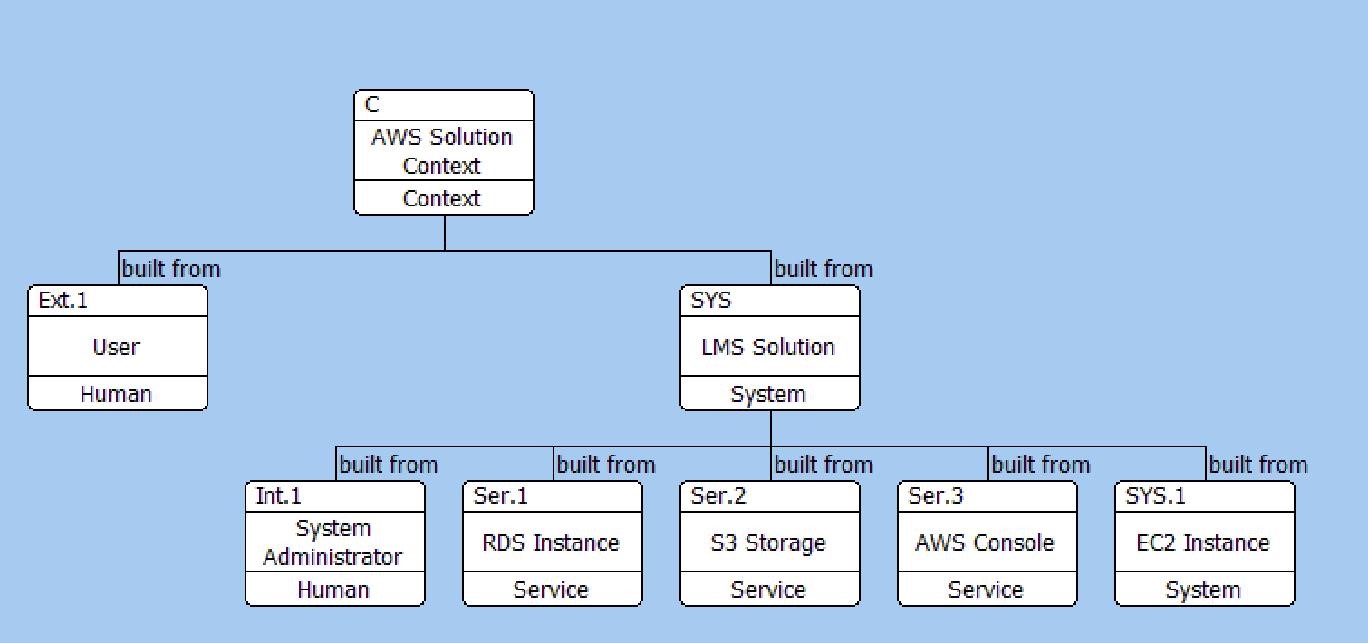
Component Hierarchy Diagram
The first step is to identify the interfaces between the elements in the solution and also the external actors interacting with our solution. In the Interface N2 diagram below we can see the interfaces when we look inside the LMS Solution.
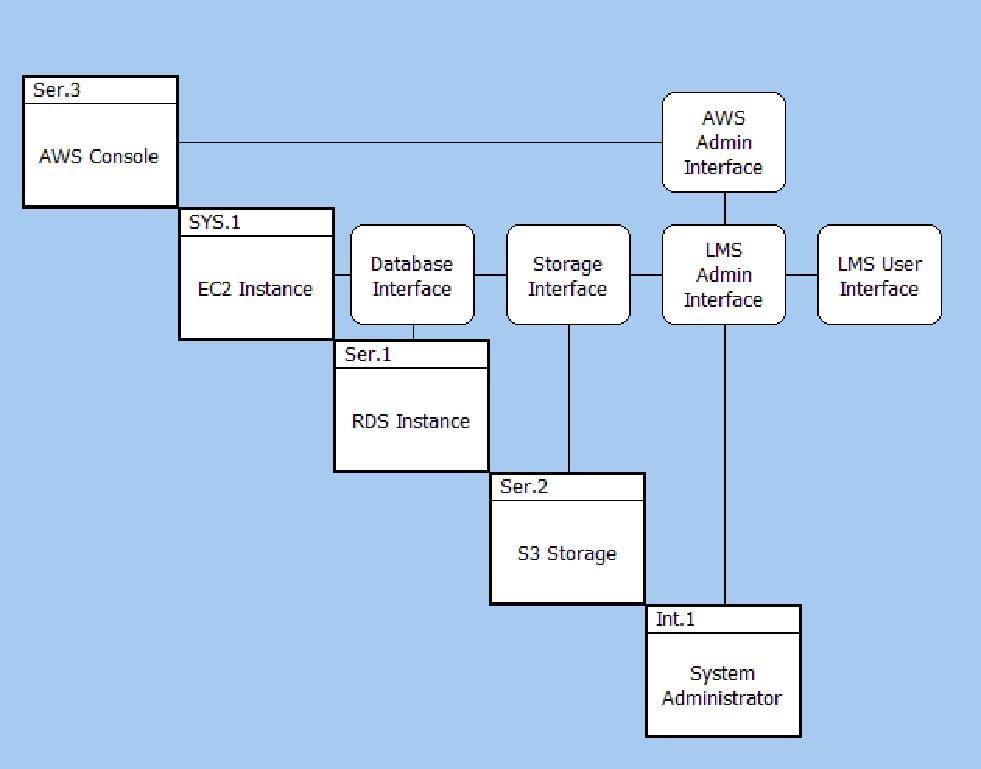
Interface N2 Diagram
An alternative view is the Interface BD. In this instance I have inserted Rounded Rectangles onto the diagram to draw the reader’s attention to the two different groups of interfaces – one associated with normal operations and the other associated with administration.
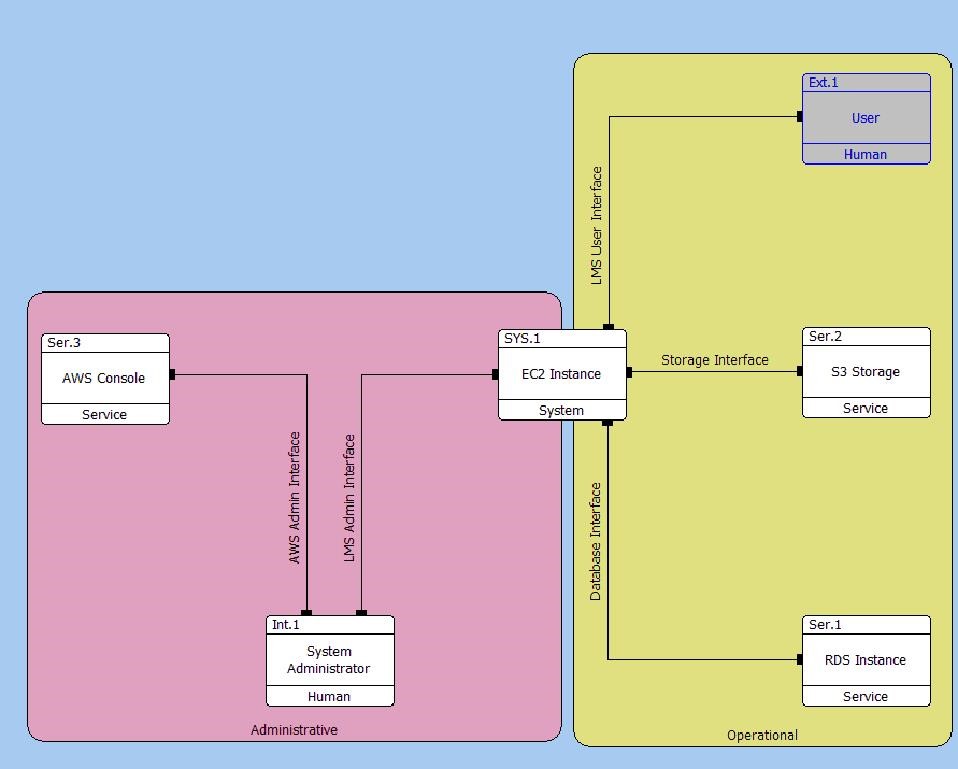
Interface Block Diagram
The interfaces represent our initial abstraction of how we expect the elements to be connected. In addition to the Description attribute for the Interface, the Joins relation also has the Ports relation attribute which can be used to record information, as shown in the image below. The information recorded in the Ports relation attribute can be displayed in the Standard BD as shown below.
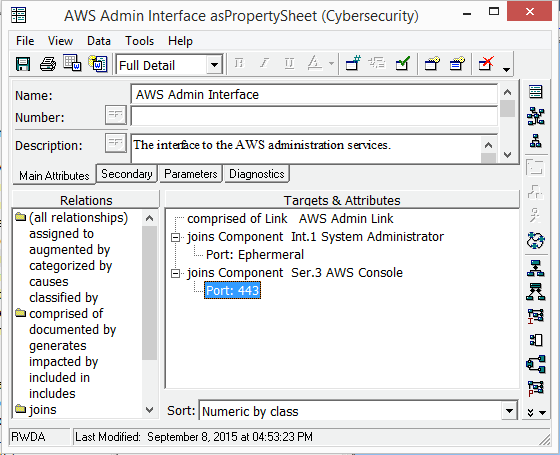
Interface Relation Properties
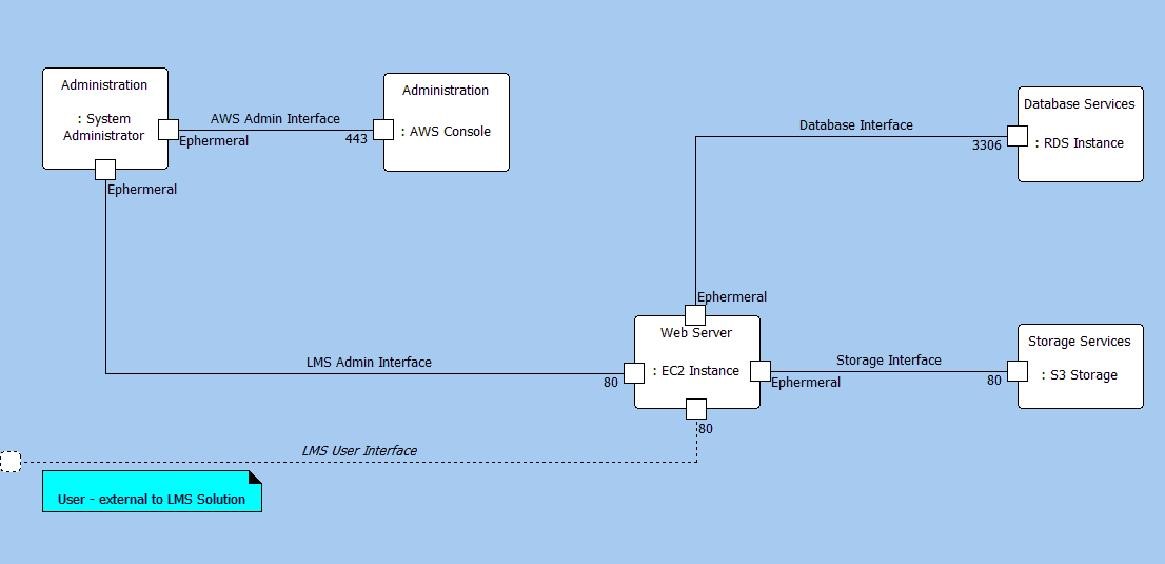
Interface Standard Block Diagram
Once our design starts to mature we can identify the mechanisms and technologies we want to use to implement the connections between the elements. These details are recorded in our model using the Link element. The Physical N2 Diagram and the Physical Block Diagram displays the relationships between the Links and the elements they connect to, as shown below.
Physical N2 Diagram
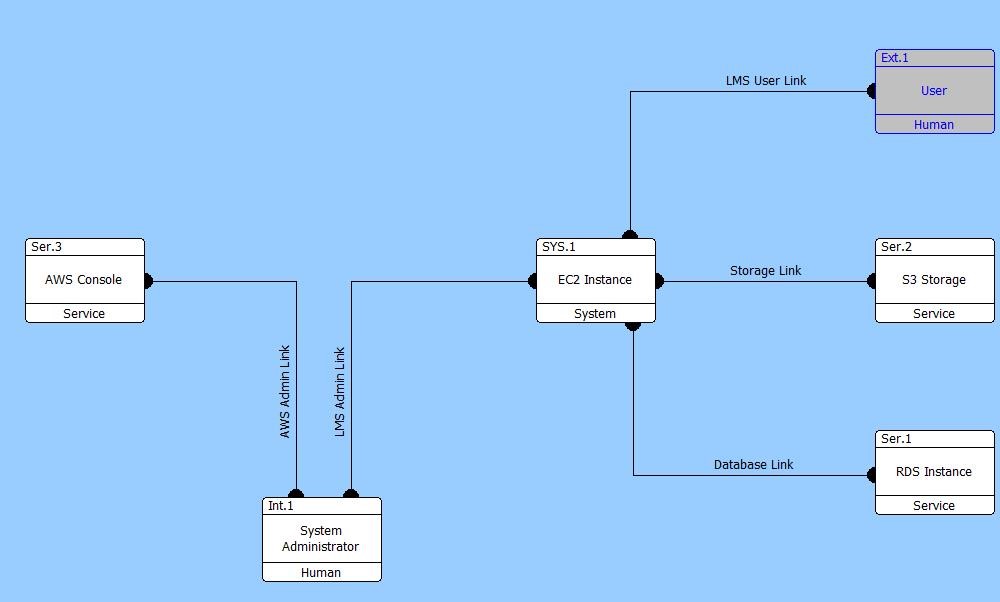
Physical Block Diagram
The Connects To relation has the Port and Direction relationship attributes which can be used to record details on the Link.
On the EFFBD I have recorded the behavior of the solution and identified the information and control signals the flow around the solution using Items. The EFFBD below shows the operational behavior and has Items as Triggers representing the events being dealt with by the solution.
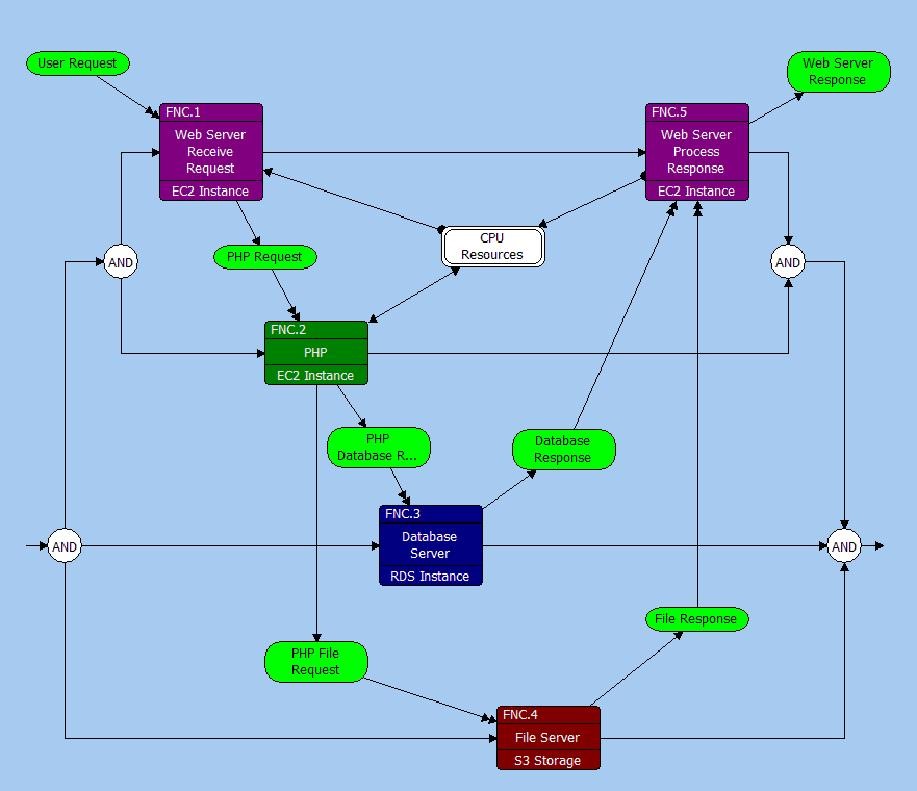
Operational Behavior EFFBD
In the EFFBD below the administrative behavior is represented in a simple abstraction. The administration actions are represented simply using Items as Data Stores.
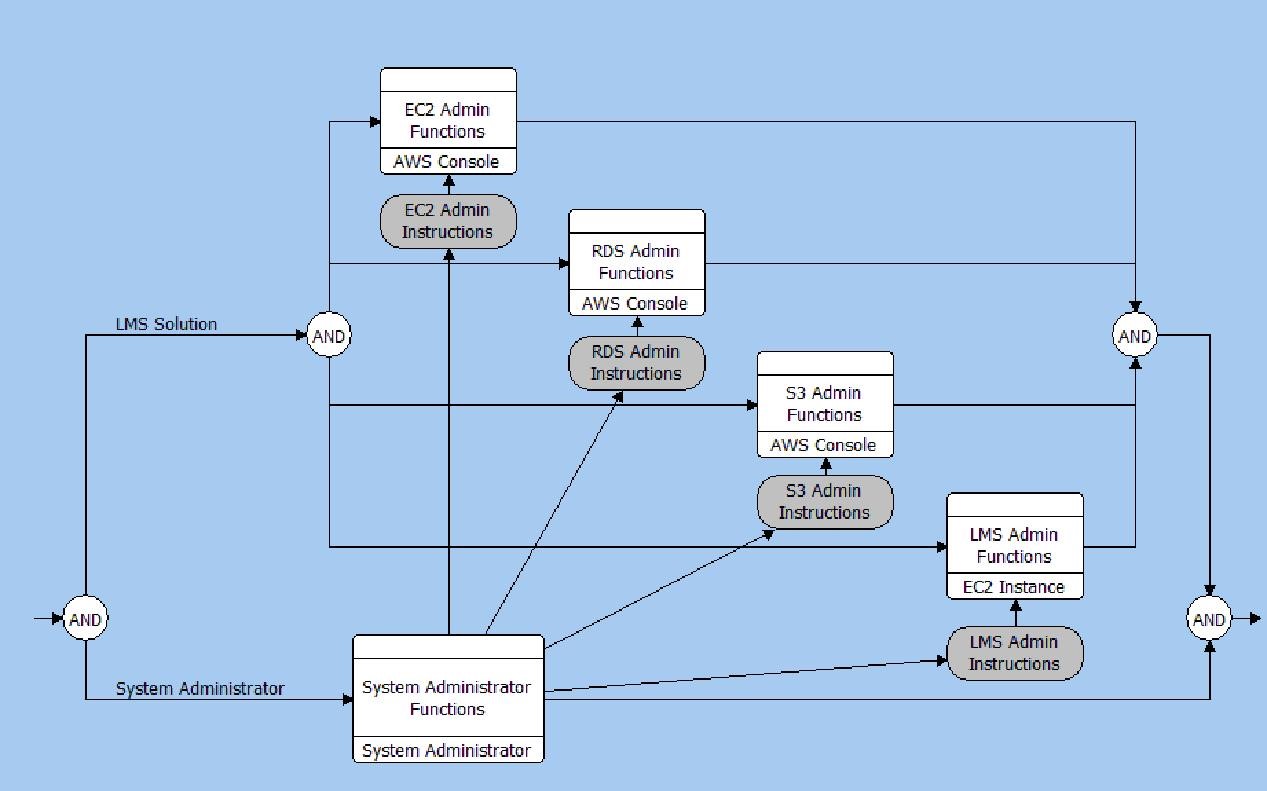
Administrative Behavior EFFBD
The relations between the Items and the Links that will transfer them is established using the Transferred By relation. The Items transferred by a Link along with the Port and Direction relation attributes on the Connects To relation are all shown on the Flow Internal Block Diagram, as shown below.
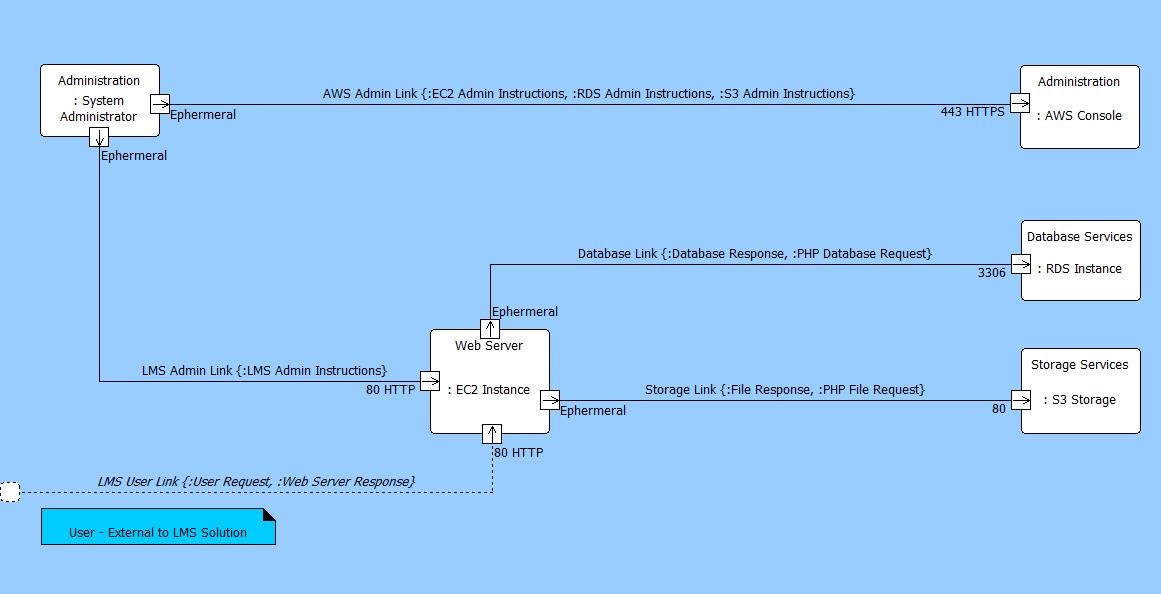
Flow Internal Block Diagram
As can be seen in the diagrams above, as our design has matured we have identified information that will be useful for implementing the cybersecurity policies for solution components such as firewalls and virtual private networks. We have information on the source and destinations of the traffic as well as the ports that are going to used. This information can be used to form the firewall rules.
While CORE/GENESYS is not going to implement your cybersecurity for you, by using the capabilities of their model, you are able to extract the information from your design in a coherent fashion to implement your cybersecurity policies.





